INFOGRAPHIC: Growing Third Party Risk
Recent shifts towards global sourcing have created countless business advantages for procurement and supply chain management teams. But the global marketplace has created additional challenges for third-party risk management programs due to the wider range of international regulations and geo-political considerations.
The infographic below explores the growing risk of third party vendors and how we help solve for it.
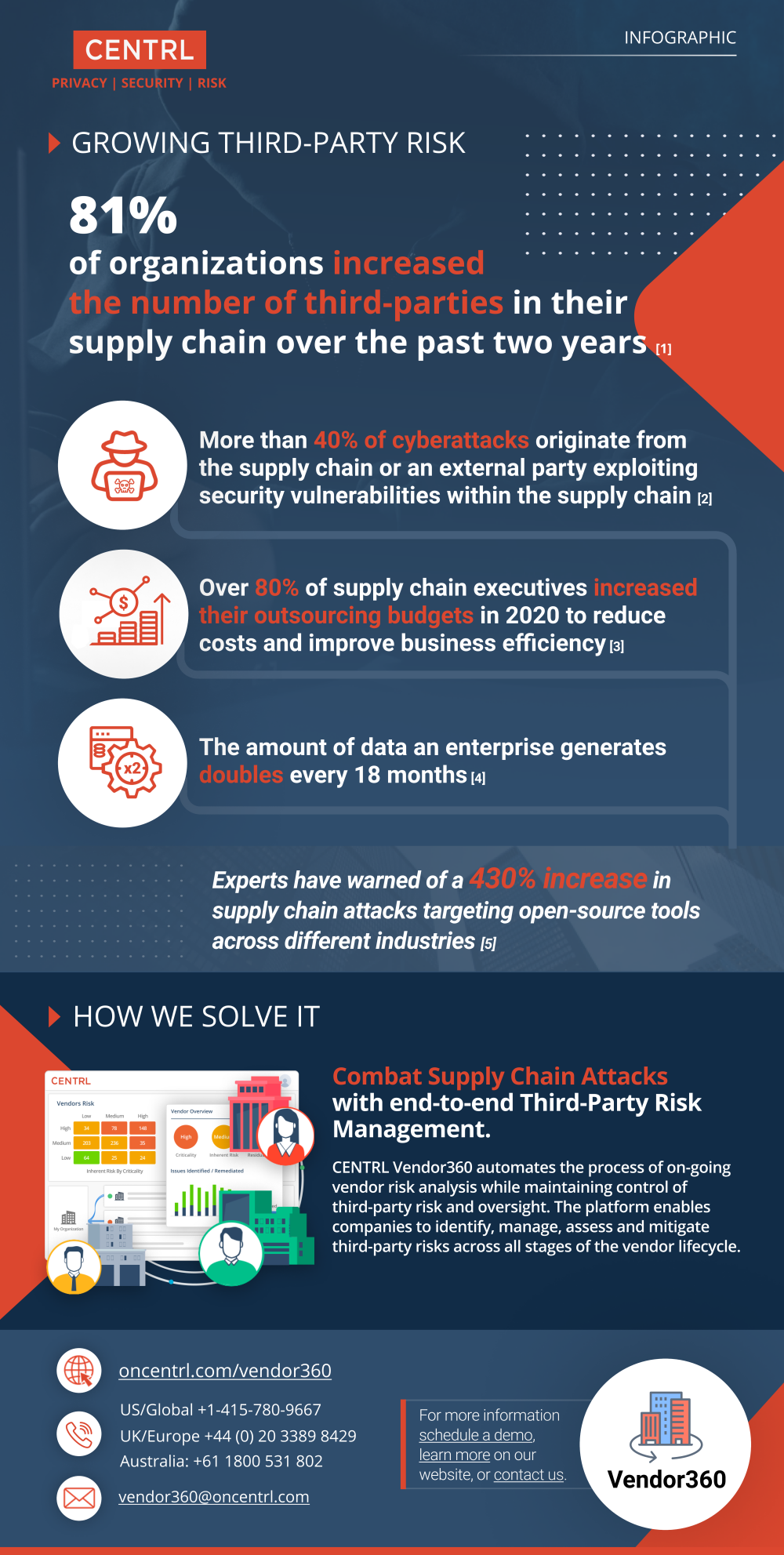
Increasing Threats from Third-Parties
More than 40% of cyberattacks originate from the supply chain or an external party exploiting security vulnerabilities within the supply chain.
Legacy third-party risk management programs have become increasingly complex and subject to human error due to high supplier adoption rates and explosive data growth. And according to a recent analysis by IDC, the amount of data an enterprise generates doubles every 18 months.
The elevated usage of third-party service providers is also challenging traditional InfoSec architecture through new backdoors into an enterprise network through the supplier. As a result, third-party service providers have emerged as popular targets for cybercriminals due to the mirrored access of sensitive business data often without the same levels of information security.
In short, digitization and globalization have intensified the risk management challenges for enterprise security and compliance teams. It has become increasingly more difficult to identify the specific points of vulnerability within complex networks of suppliers, service providers, agents, consultants, and independent contractors. This is a serious issue in your security defense. Are you prepared to protect yourself from attacks?
An Unexpected Opportunity for Analytics and Automation
However, this growth also presents an opportunity for enterprise risk management teams to utilize analytics and leverage automation to reduce the labor and resources required to conduct third-party risk management. According to a recent McKinsey research survey, about 50% of risk management functions are currently dedicated to risk-related operational processes (such as credit administration), while only 15% work in analytics. These figures are expected
to be closer towards 25% and 40% respectively by 2025 due to automated control frameworks designed to reduce human intervention and the associated costs. Getting ahead of this curve can ensure you are better armed than your competitors.
As the role of third-party service providers continues to expand within the enterprise supplier marketplace, risk management teams are exploring new solutions to efficiently mitigate risk through a comprehensive third-party risk management (TPRM) program.
End-to-End Third Party Risk Management System
CENTRL Vendor360 is a simple solution to automate the process of on-going vendor risk analysis while maintaining control of third-party risk and oversight. Our platform enables companies to identify, manage, assess, and mitigate third-party risks across all stages of the vendor lifecycle.
For more information schedule a demo, learn more on our website, or contact us.


