INFOGRAPHIC: Risk Management Operations
According to a recent study by the Institute of Internal Auditors, more than 65% of organizations “rely heavily” on third parties, yet most allocate less than 20% of their internal resources for assessing third-party risk.
The gap in these statistics is easily exploited by an evolving digital threat landscape challenging traditional security models. Digital processes have become deeply embedded into supply chain management strategies and business efficiency is increasingly more dependent on a myriad of independent third-party technology providers. The adoption of these new technologies coupled with the digitization of enterprise security is generating increasingly complex ecosystems for risk management teams to navigate.
Our latest series of infographics lays out vendor risk, compliance, and the cost to organizations. This blog post will highlight one of these infographics on how third party risk is growing and how third party risk management (TPRM) is evolving to keep up.
The infographic below highlights risk management operations and the need for automation in a successful third-party ecosystem.
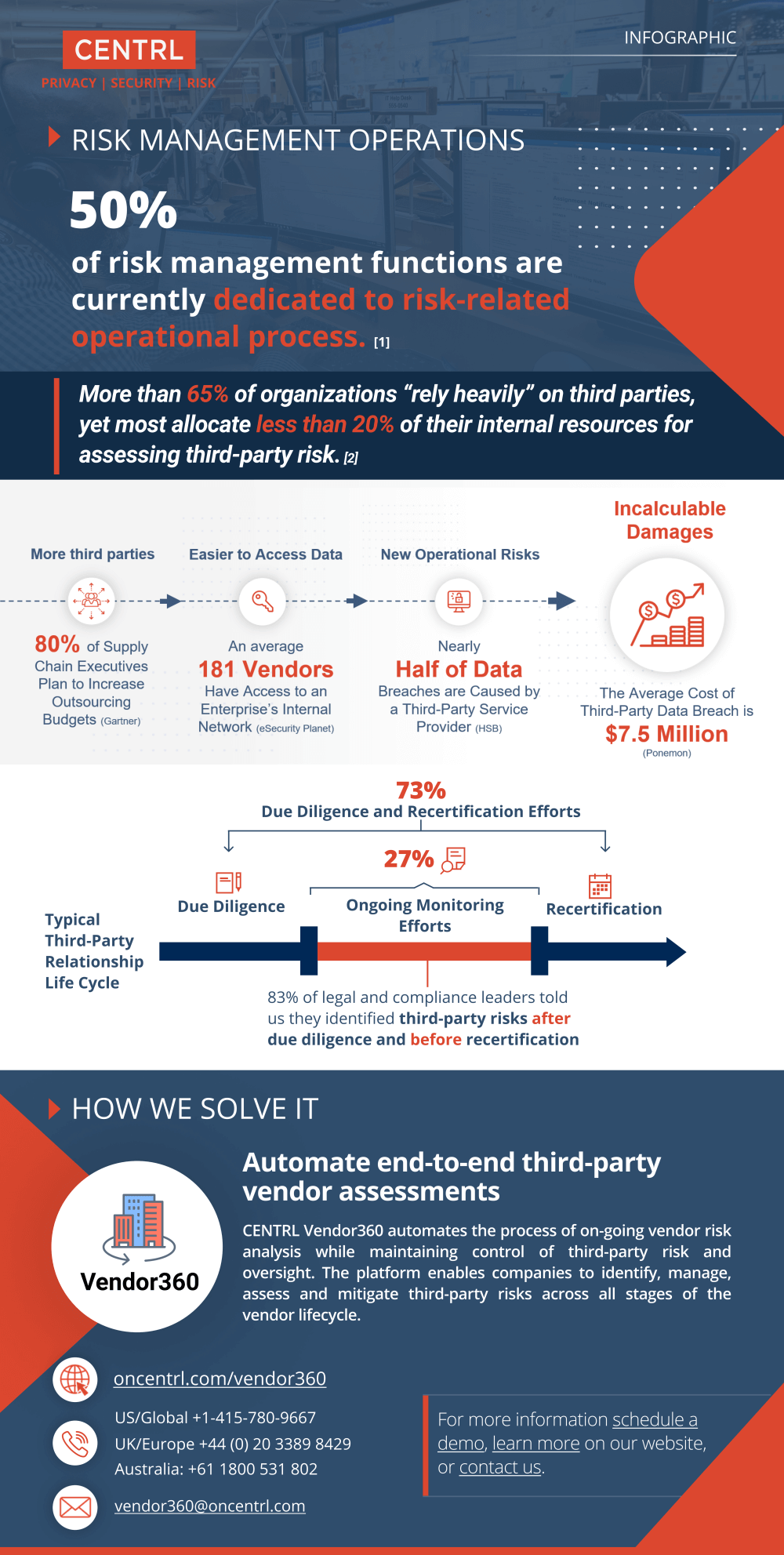
Effective Third Party Risk Management
2019 Ernst & Young survey showcases that 38% are conducting third-party risk manually. The Ponemon analysis above also indicates that an average 3.21 dedicated full-time employees are spending more than 500 hours per month completing vendor risk assessments in the healthcare industry. These manual initiatives siphon costly overhead and OPEX without the proper resources or tools required to streamline the vendor risk assessment process.
It is clear that manual TPRM initiatives cannot keep pace with an evolving third-party risk landscape intensified by new consumer privacy legislation and digital threats. Automated workflows are the fundamental foundation to addressing this challenge by simultaneously reducing third-party risk and the resources required for program management.
Increasing the Need for Due Diligence Teams
Cloud migration and server virtualization have emerged as primary drivers of third-party risk. Data breaches are regularly the result of under-provisioned operating environments without the proper security safeguards to prevent unauthorized access. This increases the emphasis on vendor due diligence teams to properly assess the wide range of digital risks associated with their third-party providers.
The cloud and open-source software economy have also globalized enterprise supply chains due to increased availability of corporate data through the internet, lowering the barriers to entry for cybercriminals across the global. As a result, enterprise risk management teams need to ensure that sensitive business systems connected to the internet are properly provisioned with the appropriate security safeguards.
Automate End-to-End Third Party Vendor Assessments
An automated approach to vendor risk management provides a clear competitive advantage by enabling enterprises to re-allocate costly compliance, InfoSec, and procurement overhead towards other strategic initiatives while simultaneously keeping pace increased rates of outsourcing, digital transformation and the rising tide of global privacy legislation.
CENTRL Vendor360 is a simple solution to automate the process of on-going vendor risk analysis while maintaining control of third-party risk and oversight. Our platform enables companies to identify, manage, assess, and mitigate third-party risks across all stages of the vendor lifecycle.
For more information schedule a demo, learn more on our website, or contact us.


