INFOGRAPHIC: The Evolving Third Party Risk Management Landscape
The convergence of data privacy regulations and third-party risk management is generating new challenges for enterprise compliance and security teams. The complexities of navigating the nuances of the shifting regulatory landscape and operationalizing the requirements are generating a considerable amount of confusion within the enterprise risk management marketplace.
Our latest series of infographics lays out vendor risk, compliance, and the cost to organizations. This blog post will highlight one of these infographics on how third party risk is growing and how third party risk management (TPRM) is evolving to keep up.
The infographic below showcases the evolving landscape of third party risk management and what you can do to automate the work.
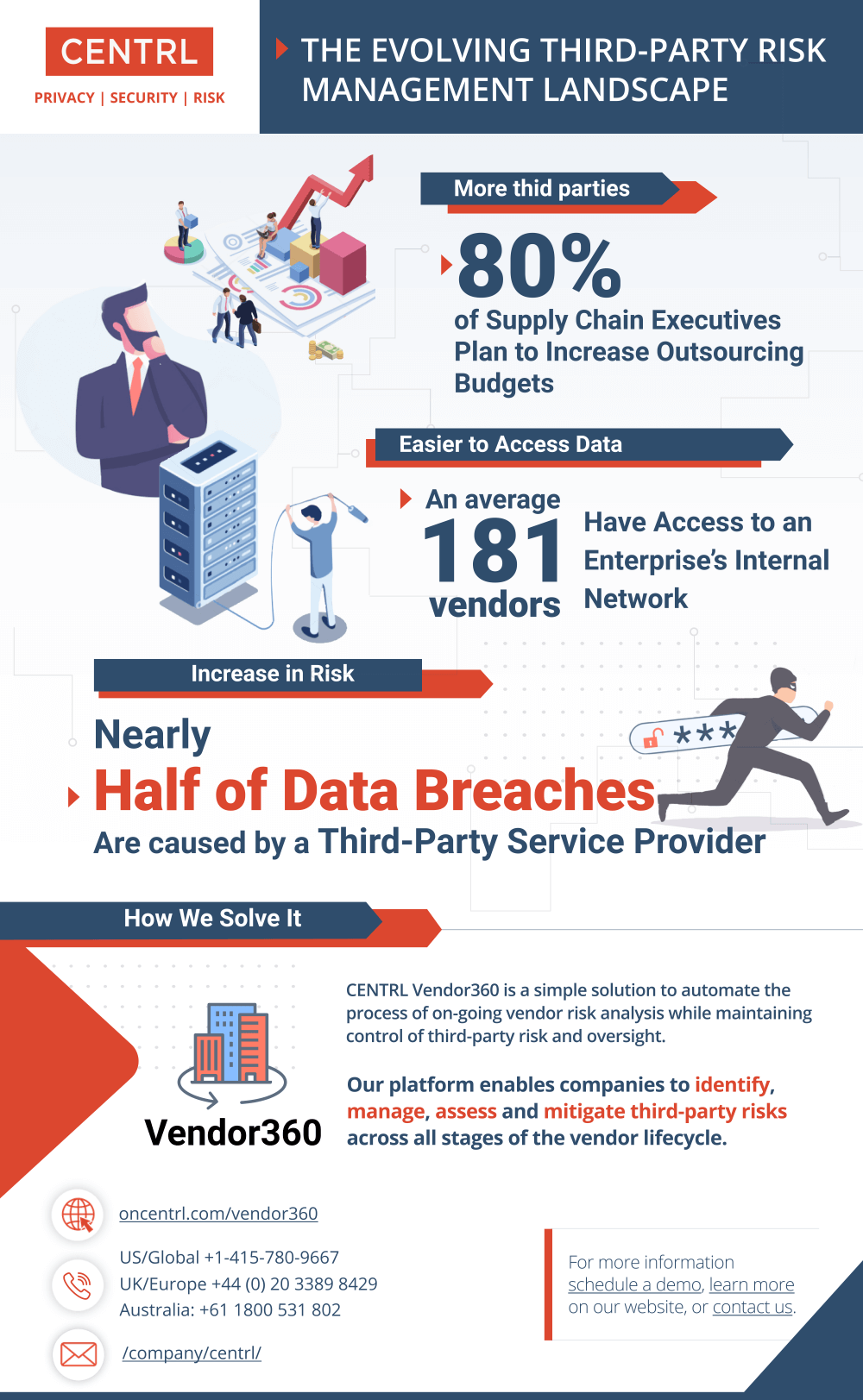
TPRM Cost is Increasing
According to a recent Gartner survey, over 80% of supply chain executives increased their outsourcing budgets in 2020 to reduce costs and improve business efficiency. But this increased efficiency can cost in the future.
According to the Ponemon Institute’s Cost of a Data Breach Report, the global average cost of a data breach was $3.86 million in the year 2020. A separate Ponemon survey from 2019 also identified that a data breach caused by a third-party was almost twice as high with an average cost of $7.5 million to remediate. These calculations include both the direct financial losses associated with the breach alongside the indirect costs including damaged business reputations, regulatory compliance fines, and lost customer trust.
The difference in these figures also highlights how third-party data breaches have a stronger correlation to potential business losses. Those dedicated to risk management continue to struggle with the eased access to sensitive business information through a third party due to the variables challenging their ability to identify, mitigate, and control risk.
Data is Easy to Access
An average of 181 vendors have access to an enterprise’s internal network. That means there are 181 areas of risk you may be unaware of. The elevated usage of third-party service providers is also challenging traditional InfoSec architecture through new backdoors into an enterprise network through the supplier. As a result, third-party service providers have emerged as popular targets for cybercriminals due to the mirrored access of sensitive business data often without the same levels of information security.
As market trends and new technology providers dictate the growing use of third-parties, enterprise risk management programs require a new approach to balance information security with business efficiency.
Vendor360 to Keep Up With the Evolving Landscape
CENTRL Vendor360 is a simple solution to automate the process of on-going vendor risk analysis while maintaining control of third-party risk and oversight. Our platform enables companies to identify, manage, assess, and mitigate third-party risks across all stages of the vendor lifecycle.
For more information schedule a demo, learn more on our website, or contact us.


